If you spend enough time reading business content online, you'll come away thinking your top priority is to be innovative, flashy, and stand out from the crowd. However, it's much more important to be safe, reliable, and trustworthy. These are qualities that will determine whether vendors or clients want to work with your company. Can you safely handle customer data? Can you ensure confidentiality?
If you run a SaaS or technology service company, SOC 2 is an excellent way to prove that you have robust data practices and organizational controls and take privacy and security seriously.
With the vast number of hacks and data breaches happening daily, more and more companies are looking to SOC 2 certification and compliance to safeguard their data. But before you can become SOC 2 certified, you need to know what SOC 2 is and how to become certified; that's what we're covering today.
What is SOC 2?
SOC 2 stands for System and Organization Controls for Service Organizations and is one of the most sought-after standards in security and compliance. It was designed by the American Institute of Certified Public Accountants (AICPA) specifically for service providers storing customer data in the cloud. This means that SOC 2 applies to any company that utilizes the cloud to store customer data, including almost all SaaS and technology services companies.
SOC2 isn't a rigid list of controls, tools, or processes, but rather it defines criteria for managing customer data based on five "trust service principles":
- Security - Firewalls, security controls, device configurations, intrusion detection.
- Availability - Disaster recovery plan, recovery tests, documented continuity, performance monitoring, security incident handling.
- Confidentiality - Data subjects, privacy, protected information, access control.
- Processing Integrity - Payment transactions, process monitoring, quality assurance, accurate processing, error detection, and correction.
- Privacy - Encryption, sector privacy rules, personal information handling, access control, two-factor authentication.
It's important to note that technically there's no such thing as SOC 2 certification, but rather, a clean SOC 2 report is generally considered a certification. SOC 2 certification is essentially a technical audit.
How Do You Get SOC 2 Certified?
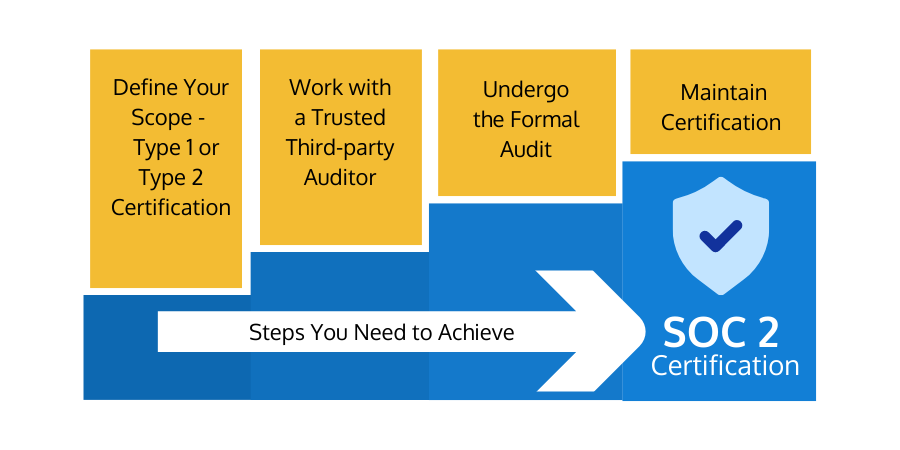
Here is your step-by-step guide to getting SOC 2 certified.
Step 1: Define Your Scope
First, you need to decide whether you need Type 1 or Type 2 certification.- Type 1 - Provides a snapshot of the privacy, security, and organizational controls at a particular point in time (when the audit is carried out). It assesses whether your organizational controls are sufficient in helping the company meet its goals.
- Type 2 - Assesses the same organizational controls over a fixed period, typically one year.
Step 2 - Contact Auditors and Build a Roadmap to Compliance
The next step is to find an experienced SOC 2 auditor. Once you've found the right auditor, you should build a roadmap to achieve SOC2 compliance. This will take some time (multiple weeks or even months). Once you've built your SOC 2 compliant processes, you need to follow them to the letter.An essential part of this process is familiarizing yourself with the SOC 2 report structure:
- System Description - A description of your entire system based on the description criteria and trust principles.
- Management's Assertion - This is the assertion from high-ranking employees that your description and controls match the required criteria.
- Opinion Letter - This is the auditor's opinion on whether you meet compliance standards. It's usually the first thing you see when you get your SOC 2 Report.
- Other Information - Any additional information on controls.
- Description of the Tests - Which tests were conducted to assess your controls and security measures.

 Batoi Corporate Office
Batoi Corporate Office