In today’s interconnected world, Identity and Access Management (IAM) isn’t a luxury - it's a necessity. With the rise of cyber threats, ensuring secure and convenient access to digital resources is paramount. That's where Batoi’s cutting-edge IAM and SSO solutions come into play. In this blog post, we'll delve into why these solutions are vital for your organization’s digital security and efficiency.
The Importance of IAM
IAM is the cornerstone of any robust digital security strategy. It allows you to manage who has access to what within your organization. A well-implemented IAM system can boost productivity, enhance security, and even help with compliance issues. Simply put, it's not just about keeping the bad guys out; it's also about letting the right people in efficiently and securely.
SSO: One Password to Rule Them All
Single Sign-On (SSO) is another game-changer. Say goodbye to password fatigue because SSO requires only one set of credentials to access multiple services. Batoi's SSO solutions support various third-party platforms like Google, Microsoft, and Facebook, making it a breeze for users to log in with their existing accounts.
Unparalleled Security with MFA
Multi-factor authentication (MFA) adds an extra layer of security by requiring two or more forms of verification. At Batoi, we offer MFA that goes beyond the traditional SMS-based authentication. Our solutions leverage advanced biometric technologies for a safer and more user-friendly experience.
Biometric and Face Recognition: The Future is Now
Our IAM solutions aren't stuck in the past; they're geared for the future. We employ state-of-the-art biometric and face recognition technologies to ensure that your security is never compromised. With the help of machine learning algorithms, these authentication methods are not just secure but incredibly efficient.
Behind the Scenes: The Architectural Aspects of Batoi's IAM and SSO Solutions
Layered Approach
We've designed our solutions with a layered architectural approach, allowing for optimal scalability, security, and adaptability.
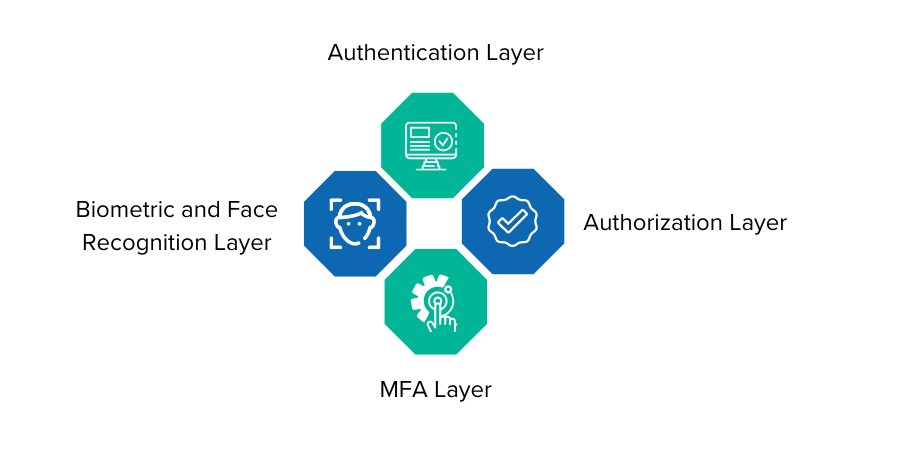
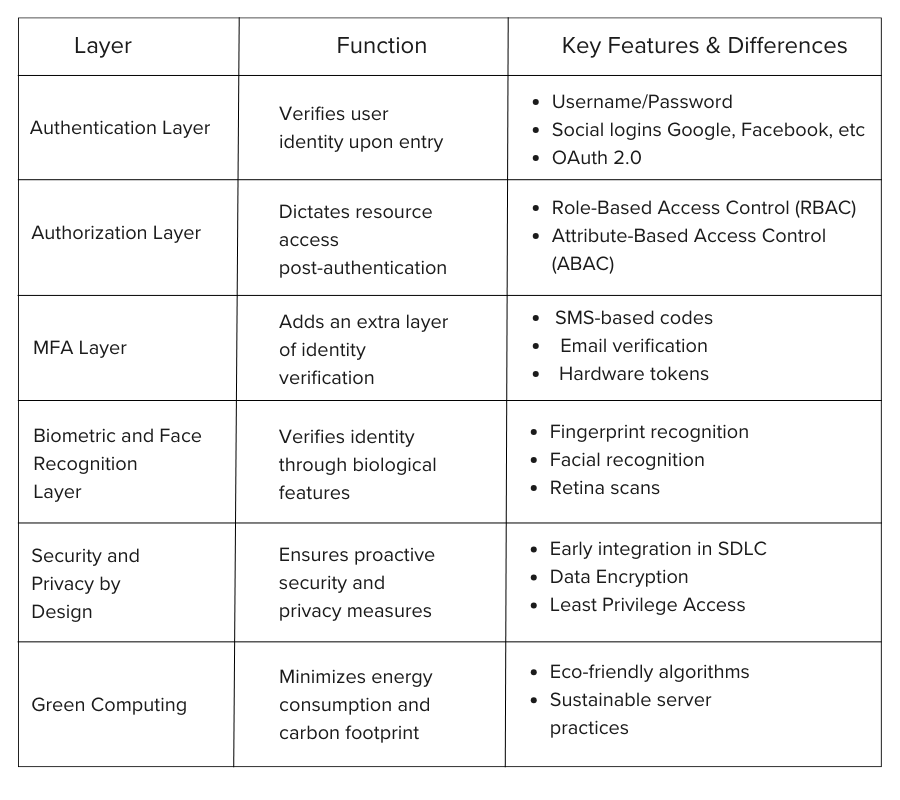
Authentication Layer: This is the entry point, where user identities are verified using traditional methods like username/password and advanced techniques like MFA and biometrics.
Authorization Layer: This layer dictates what resources the user can access after authentication. It employs Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) to granulate permissions based on user roles and attributes.
MFA Layer: Our Multi-Factor Authentication layer integrates seamlessly with the Authentication layer, adding an extra shield of security through various verification methods such as SMS, email codes, or even biometric data.
Biometric and Face Recognition Layer: Utilizing machine learning algorithms, this advanced layer verifies identity through biological features like fingerprints, facial patterns, or even retina scans, making it extremely difficult for unauthorized users to gain access.
The following table can serve as an easy-to-understand snapshot of the intricacies of your IAM and SSO solutions.
Technology Stack
Built predominantly on an Open Source tech stack (Linux, Apache, PHP, and MySQL) foundation, our IAM and SSO solutions leverage cutting-edge technologies, including:
- OAuth 2.0: For secure and standardized third-party integrations
- JWT: JSON Web Tokens for stateless, secure data interchange
- OpenID Connect: For advanced identity layer on top of OAuth 2.0
- DevSecOps Principles: Integrated security measures throughout the development life cycle
Flexibility and Customization
The modular architecture allows for extensive customization and integration, which means the system can adapt to your organization's unique needs without requiring a complete overhaul.
Green Computing and Sustainability
Aligned with our commitment to sustainable practices and green computing, the architecture is designed to be energy-efficient, minimizing the resource footprint both on the client and server sides.
Security and Privacy by Design: Core Principles in Batoi’s IAM and SSO Solutions
Security by Design is an approach that integrates security measures throughout the entire lifecycle of a system or software. Instead of adding security protocols as an afterthought or a final step, we ensure that each layer of our architecture is built with security in mind right from the get-go. Privacy by Design goes hand-in-hand with Security by Design. It emphasizes the protection of user data by incorporating privacy features and controls into the development and operational practices. It ensures that privacy concerns are addressed proactively, not reactively.
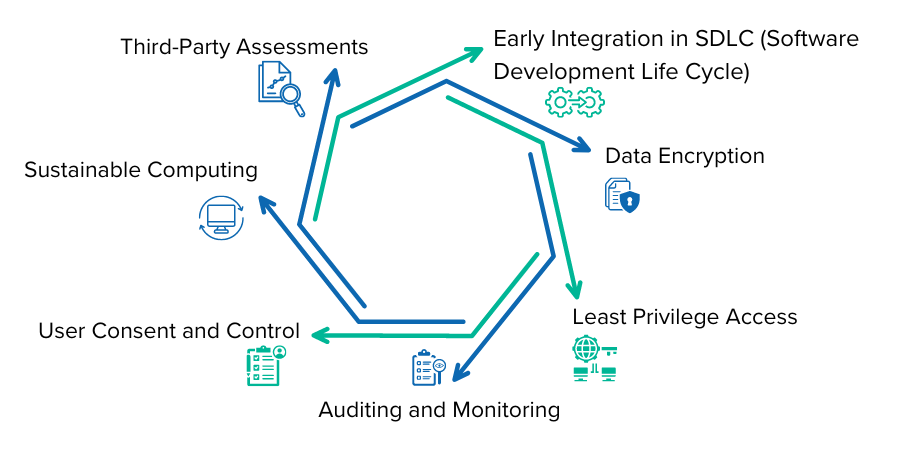
How We Achieve Security and Privacy by Design
Early Integration in SDLC (Software Development Life Cycle): By adhering to DevSecOps principles, security measures are implemented from the earliest stages of development, mitigating risks before they become threats.
Data Encryption: Data at rest and in transit are encrypted using advanced cryptographic algorithms, ensuring that sensitive user data remains confidential and secure.
Least Privilege Access: Our Authorization layer employs the principle of least privilege, meaning users are given the minimum levels of access necessary to perform their tasks.
Auditing and Monitoring: Continuous monitoring and auditing capabilities are built into the system. Any abnormal activity triggers real-time alerts, allowing for quick remedial action.
User Consent and Control: The system is designed to provide users with control over their data. Features such as data portability and erasure are integrated, aligning with GDPR and other global privacy standards.
Sustainable Computing: Eco-friendly algorithms and practices are implemented to minimize energy consumption and carbon footprint, aligning with our commitment to green computing.
Third-Party Assessments: We undergo regular security audits and privacy impact assessments from independent third parties, ensuring our solutions are up-to-date with global security and privacy standards.
Continuous Updates
Both security and privacy landscapes are continually evolving. Therefore, our solutions are designed for easy updates and scalability to adapt to new challenges and regulations as they arise.
Why Choose Batoi?
- Future-Ready: Our solutions are scalable and built to adapt to emerging technologies.
- Compliance: Ready to meet global standards like GDPR, CCPA, and HIPAA.
- Customization: We offer highly customizable solutions tailored to fit your specific needs.
Conclusion
As digital landscapes evolve, so do the challenges and opportunities in identity and access management. By adopting Batoi's advanced IAM and SSO solutions, you’re investing in a more secure and efficient digital future.

 Batoi Corporate Office
Batoi Corporate Office