Organizations are constantly threatened with data loss and disruption due to security breaches. With more sophisticated attacks, the proliferation of remote working, extortion of confidential data, security intricacies, unrelenting threats, etc., are rising.
Many organizations have the necessary experts and resources to safeguard themselves but facing budget constraints. Thus, businesses are inclined toward outsourced services for Managed Detection and Response solutions.
MDR is one of the fastest-growing categories in the cybersecurity market, where organizations outsource their critical security operations to third-party providers. This article details how MDR can provide 24*7 security controls and cloud-managed services.
What are MDR Services?
Managed Detection and Response (MDR) is a managed 24*7 service comprising threat monitoring, detection, and response aimed to help businesses with their incident response (IR) requirements.
Illustrating outsourced cybersecurity services, (MDR) services are designed to protect confidential data and critical business IT assets, even if a threat evades organizations’ security postures. MDR services bring together advanced analytics, threat intelligence, and human knowledge in incident investigation and response at the host and network levels.
MDR services deliver modern security operations center (MSOC) activities to customers remotely while equipping enterprises with unique capabilities to identify, evaluate, investigate, and proactively respond to threats through threat mitigation and containment. MDR service providers deliver a turnkey experience via a pre-determined technology stack such as endpoints, networks, and cloud services to accumulate pertinent logs, data, and contextual information. This telemetry is evaluated with various tools/methods within the provider's platform. This process enables threat hunting and incident management experts to investigate and generate preventive actions.
Recently, MDR services have witnessed colossal visibility and accountability as enterprises recognize the criticality of 100% protection against threats. The scale and complexity of the security challenge become uncontrollable for enterprises, regardless of size.
An effective MDR solution protects on-premises, cloud systems, and endpoints. It provides optimal security capabilities that are easier to deploy and scale up for detecting critical threats hidden in thousands of events. However, enterprises are not required to configure, upgrade, or comprehend the complexity of ingesting, standardizing, distilling, and analyzing massive security data to make MDR operational effectively.
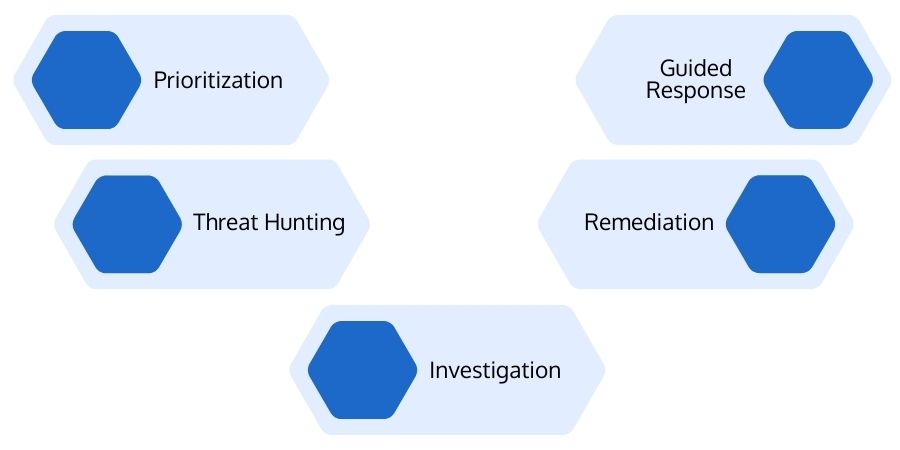
How Does MDR Work?
Below are the significant capabilities MDR security services can offer:
Prioritization
Managed prioritization, or Managed Endpoint Detection and Response (EDR), assists enterprises in rectifying a bulk of threat alerts while determining which alert must be addressed on a priority basis. Managed EDR services implement automated standards in conjunction with a human inspection to distinguish between false positives and gentle events from actual, high-risk threats.
Threat Hunting
Human threat hunters have the knowledge and abilities required to identify ambiguous threats. They provide in-depth inferences required to detect what layers of automated defenses are missed.
Investigation
Managed investigation assists enterprises in comprehending the threats’ scope and details. This is often accomplished by sending security alerts with additional context. This is required to plan an effective threat response.
Guided Response
The guided response is aimed to provide actionable guidance on how to mitigate a specific threat appropriately. These services render proper guidance over a variety of security incidents. For example, they can recommend isolating an affected system from the security network and providing precise instructions to remove a threat or recover from an attack.
Remediation
In the final phase, remediation is performed for incident response. Managed remediation aids in restoring your system to its pre-attack state. It incorporates cleaning a registry, deleting a malware, removing persistence mechanisms, and ejecting invaders. They prevent additional security sacrifices while returning the network to a reliable state.
MDR Benefits
With MDR, organizations can reduce their time-to-detect and time-to-respond from months to a few minutes. Some typical benefits are the following:
- By improving security configuration and eliminating rogue systems, organizations can enhance the security posture and become more resilient to potential, rigid attacks.
- Steadily managed threat hunting spots and mitigated hidden, sophisticated threats.
- With remediation and response guidelines, organizations can respond to security issues more effectively while restoring systems to regular functioning.
- Benefit from specialist security expertise, which would be difficult and expensive to employ an in-house specialist.
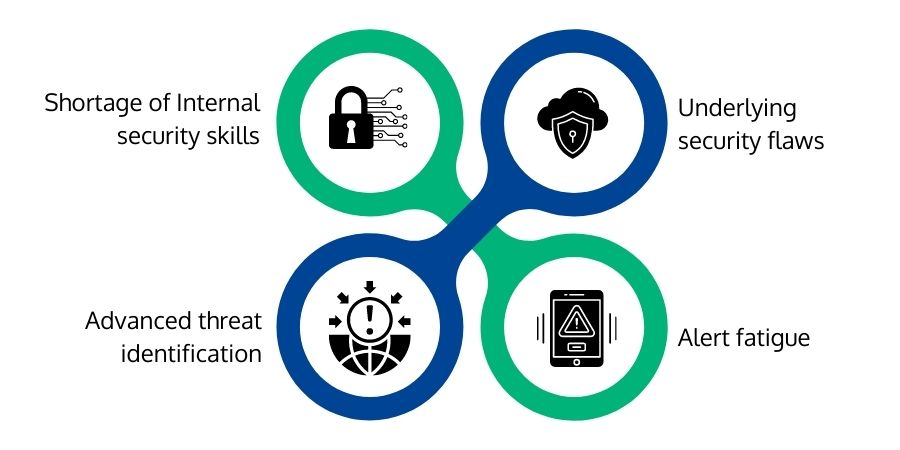
What Challenges Do MDR Solutions Address?
When attempting to create a complete cybersecurity program, organizations confront multiple challenges that MDR services can solve:
Shortage of Internal Security Skills:
The scarcity of cybersecurity talent puts organizations in a position to find and retain experienced cybersecurity personnel; it’s both complicated and resource-intensive as organizations grapple with employing these experts, even with substantial budgets. MDR ensures that organizations can immediately enhance their security expertise and workforce.
Advanced Threat Identification
Many sophisticated attacks use the latest tools and tactics, enabling threat actors to remain undetected via conventional security systems. MDR services can detect and remediate these threats using proactive threat hunting.
Underlying Security Flaws
Inefficient security practices can expose businesses to underlying security assaults where MDR services continually monitor the infrastructure's attack surface and proactively look for threats. They assist organizations in identifying these issues and recommend preventive actions. Correct them.
Alert Fatigue
Conventional security solutions generate an excessive number of security alerts, including a high number of false positives. It resulted in alert fatigue, where security personnel avoided several alerts. MDR services provide the necessary expertise to examine all relevant alerts, identify breaches, and contain them before they cause harm.

 Batoi Corporate Office
Batoi Corporate Office