Introduction
Vulnerability management is a necessary evil that enterprises must consider seriously to mitigate business risks. Finding and prioritizing vulnerabilities is an ongoing process to evaluate and manage risk. According to 2021's record-breaking report, more than 28,695 vulnerabilities got disclosed last year. Among them, nearly 4,100 are remotely exploitable & have a severity level of either high or critical. Thus, finding and prioritizing vulnerabilities have become an essential practice to identify threats and reduce the attack surface to a significant level. This article will give you a quick walk-through of the steps to find and prioritize website vulnerabilities and what essential questions to ask while prioritizing website vulnerabilities.
Defining Website Vulnerabilities
Website vulnerabilities are bugs, weaknesses, or flaws in a company's website or web application. Website vulnerabilities can occur due to not validating or sanitizing form inputs, integrating malicious dependencies, API and web server misconfigurations, design flaws, etc. Attackers may exploit these vulnerabilities to disturb the standard flow of the business or for monetary benefit by stealing sensitive data and selling them on the dark web.
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Security Misconfiguration
- Insecure Direct Object References
- Broken Authentication and Session Management
- Insecure Cryptographic Storage
- Failure to Restrict URL Access
Finding and Prioritizing Website Vulnerabilities
Finding and prioritizing vulnerability is an essential practice and element of a vulnerability management program. Today, all modern enterprises have websites and web applications through which they do the branding, provide their services, or deliver their product to the end-users. Almost all enterprises harbor different website vulnerabilities that can cost if exploited or may damage the brand reputation. Finding, managing, and resolving all such website vulnerabilities of distinct severity-level are impossible.
Therefore, companies use the prioritizing technique to categorize website vulnerabilities based on criticality. Here's a step-wise approach to a vulnerability management program that most enterprise leverages to find and prioritize different flaws and aims to minimize threats significantly.
- Enterprises should identify all the vulnerabilities in their website. Identifying vulnerabilities uses standardized services and techniques like:
- Vulnerability scanning
- Penetration testing
- Web application assessment
- Network mapping
- Database assessment
- Server/cloud security scanning
-
Scanning for other similar website vulnerabilities by referring to the Common Vulnerabilities and Exposures (CVE) database
-
Prioritizing the vulnerabilities as per risks
- Remediating the vulnerabilities as per severity level through patch management programs
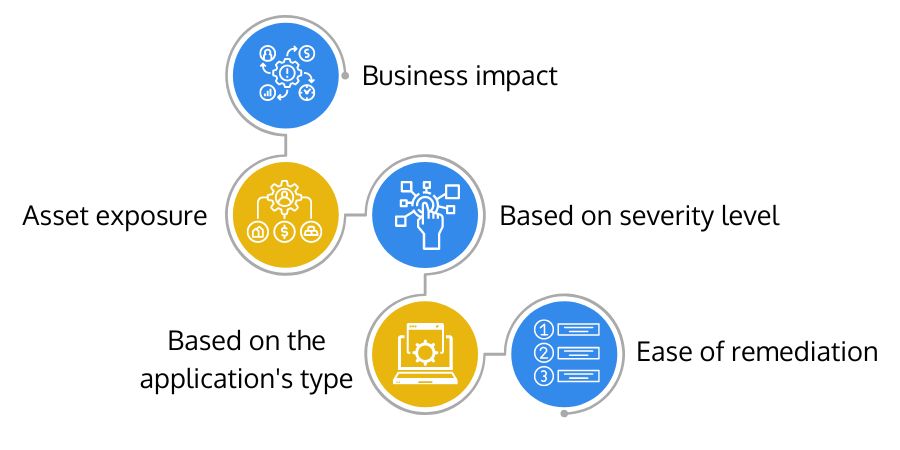
Factors on which enterprises prioritize website vulnerabilities –
There are five primary factors based on which enterprises prioritize website vulnerabilities. These are:
- Business Impact: Enterprises often prioritize website vulnerabilities as "critical" if those hamper the usual business workflow or disturb the services or products the business caters to its customers. That is one scenario where they want quick remediation or patch management to reduce the risk.
- Asset Exposure: Another reason based on which enterprises prioritize website vulnerabilities is asset exposure. If any vulnerability exposes private corporate assets to the internet openly or if the cybercriminal can leak all confidential corporate information publicly, such website vulnerabilities become critical and require an immediate solution and fixes.
- Based on Severity Level: Many website security professionals depend on CVE ratings to determine which website vulnerability needs an immediate fix. Some enterprises also define their slabs and criteria for measuring the severity level of website vulnerabilities. The most common slabs for measuring vulnerability severity levels are: low, medium, high, and critical.
- Based on the Application's Type: Often the security team prioritizes website vulnerabilities based on the sensitive data the application or its component (database, server, etc.) is holding. This methodology depends on the parameter, such as how much sensitive data will get exposed if cybercriminals exploit the vulnerability.
- Ease of Remediation: Another approach that some companies prefer to prioritize vulnerabilities is those that are easiest to fix. They prioritize the list based on these criteria to patch as many website vulnerabilities as possible. Such an approach does not guarantee it will address the most pressing issues.
Common brainstorming questions to ask while prioritizing website vulnerabilities.
Contextual information about the website's vulnerability is essential to determine if it is a real threat or not. Such information also gives a clear picture of how much damage such flaws can cause to the organization. The vulnerability management team should ask a set of well-known questions before prioritizing the vulnerability.
- What is or could be the severity level of the threat?
- How common is the website vulnerability, and what problem can it cause to the organization's assets?
- Whether penetration testing & vulnerability scanning techniques enough to detect the vulnerability?
- To what vector can the website vulnerability expose the assets and sensitive data of the organization?
- How much time does this website vulnerability require to disclose the sensitive data?
- What could be the possible attack vectors that cybercriminals leverage this vulnerability?
- What are the various mitigation techniques available for resolving this threat?
Conclusion
We hope this article has given you a crisp idea and insight into the different approaches enterprises take to prioritize website vulnerabilities and related questions that ask to brainstorm within the team to get the right track in solving such vulnerabilities. Understanding the right approach and prioritizing website vulnerabilities with best practices can help remediate security threats.

 Batoi Corporate Office
Batoi Corporate Office