
SIEM is a monitoring and analysis system for security and auditing. It is becoming a common security technique due to the recent increase in cyber threats and tighter security requirements.
SIEM has evolved to become more than the log management systems. Leveraging AI, SIEM enables advanced user and entity behavior analytics. It's a powerful data orchestration solution for dealing with constantly changing risks and regulatory compliance and reporting.
In this blog, we shall discuss the concept of SIEM, how it works, and its benefits.
A Glance at SIEM
SIEM stands for Security Information and Event Management - offers next-generation detection, analytics, and response capabilities to businesses.
Combining Security Information Management (SIM) and Security Event Management (SEM), SIEM provides a real-time analysis of security events generated by applications and network devices and tracking and logging of security data for compliance or auditing purposes.
SIEM software compares events to rules and analytics engines, indexes them for secondary search, and allows sophisticated threats to be detected and analyzed by globally accumulated intelligence.
By providing data analysis, event correlation, aggregation, reporting, and log management, security teams may get insight into and keep track of the actions in their IT environment.
How Does SIEM Work?
Specifically, all SIEM solutions perform some sort of data aggregation, fortification, and classifying functions to reveal threats and comply with data compliance regulations. While different solutions have different capabilities, most offer the same set of functionalities:
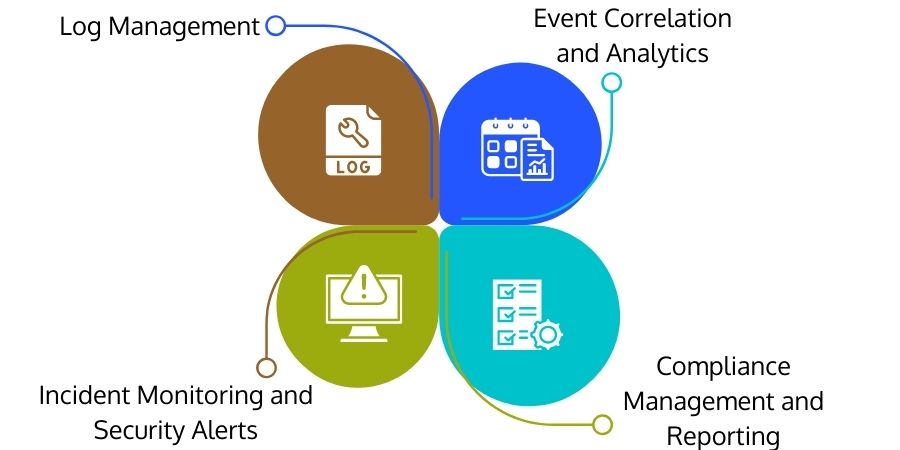
Log Management
SIEM collects event data from various sources within an organization's network. For example, logs and flow data from users, applications, assets, cloud environments, and networks are collected, stockpiled, and scrutinized in real-time, allowing IT and security teams to centrally manage their network's event log and network flow data.
Some SIEM solutions additionally connect to third-party threat intelligence feeds and allow them to compare their internal security data to previously identified threat signatures and profiles. After that, teams can block or detect new attack signatures by integrating with real-time threat feeds.
Event Correlation and Analytics
Event correlation is an integral component of any SIEM solution. It gives insights to swiftly find and mitigate possible threats to enterprise security by utilizing advanced analytics to identify and analyze intricate data patterns.
SIEM systems reduce IT security teams' mean time to detect (MTTD) and mean time to respond (MTTR) by offloading the manual operations involved with in-depth security event analysis.
Incident Monitoring and Security Alerts
SIEM solutions can rectify all entities and assets in the IT ecosystem and provide centralized control of on-premise and cloud-based infrastructure. SIEM technology can monitor security incidents across all connected people, devices, and applications while identifying suspicious activities.
Administrators can be promptly alerted using customizable, established correlation rules and take appropriate action to control the situation before it becomes a more severe security risk.
Compliance Management and Reporting
SIEM solution is a popular choice for businesses subjected to various regulations. It is a powerful tool for obtaining and validating compliance data across the corporate infrastructure as it allows automated data collection and analysis.
SIEM solutions can create real-time compliance reports for PCI-DSS, GDPR, HIPAA, SOC, and other compliance requirements mitigating security management risks and detecting potential violations earlier. Many SIEM solutions include exclusive pre-built add-ons that can generate automatic reports to meet compliance needs.
Why SIEM - Its Benefits
It is critical to inspect and mitigate IT security risks proactively. SIEM solutions benefit organizations and have become an integral element in streamlining security workflows. Some benefits are the following:
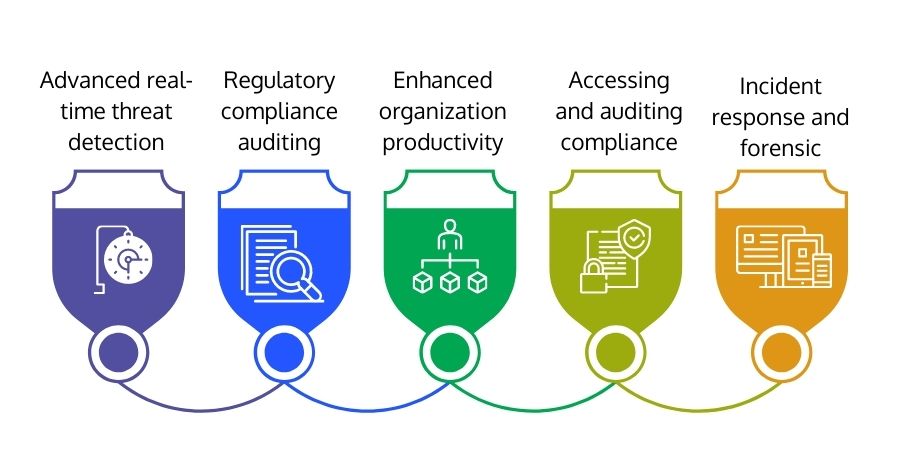
Advanced Real-time Threat Detection
SIEM monitoring solutions deployed across complete infrastructure help boost security posture by reducing the time it takes to identify and respond to potential network attacks and vulnerabilities.
Regulatory Compliance Auditing
SIEM solutions provide centralized compliance auditing and reporting for the organization's complete infrastructure. Advance automation simplifies the collection and inspection of system logs and security events to diminish internal resource consumption while maintaining stringent compliance reporting standards.
Enhanced Organization Productivity
SIEM is a crucial driver to enhancing interdepartmental efficiencies as it improves the visibility of the IT landscape. It enables teams to communicate and coordinate promptly when responding to perceived events and security problems with a single, unified view of system data and integrated security orchestration, automation, and response (SOAR).
Accessing and Auditing Compliance
Compliance auditing and reporting is a critical yet challenging task for many organizations. SIEM solutions could reduce the resource costs required to manage this process by providing real-time audits and on-demand regulatory compliance reporting whenever required.
Incident Response and Forensic
SIEM solutions detect and alarm when an attack is in process. Forensic analysis tools within SIEM evaluate historical data to discover past breaches and report on what cyber thefts have accessed. Some built-in features help analyze diverse attacks and suggest preventive actions to prevent them from progressing.
SIEM Software/Tools
SIEM software gathers and organizes log and event data to aid in detecting and tracking security breaches. It's a practical approach for gaining security insights.
There are a variety of security information and event management solutions in the market; some of them are:
ArcSight
ArcSight collects and analyses log data from security technologies, operating systems, and applications in a company. The technology notifies security workers when a malicious threat is discovered.
ArcSight can initiate an automatic response to prevent harmful activities. It also incorporates third-party threat intelligence feeds for more precise threat detection.
QRadar
It is a software program developed by IBM. IBM QRadar collects log data from network devices, operating systems, applications, and user actions in an enterprise's information system.
QRadar SIEM analyses log data in real-time, allowing users to spot and halt assaults rapidly. It can also gather network flow statistics and log events from cloud-based apps.
Splunk
Splunk Enterprise Security tracks the dynamic actions associated with sophisticated security threats by providing real-time threat monitoring, quick investigations using visual correlations, and investigative analysis.
Splunk SIEM is offered as software that can be installed locally or as a cloud service. It allows third-party programs to integrate threat intelligence feeds.
Ending Notes
A SIEM system can detect cyber-attacks, breaches, and data exfiltration events in real-time if properly deployed and, more importantly, monitored and exploited. SIEM solutions make a wider variety of network and cyber security tools accessible. They give you a birds’ eye perspective of network and application security.
From small SOC teams to huge multinational IT departments, organizations employ SIEM systems to expedite their threat detection and response to reduce risk to the business substantially.
However, SIEM technologies are resource-intensive; they require professional employees to implement and administer and increase support and training services.

 Batoi Corporate Office
Batoi Corporate Office